Security Content
5 Great Reasons to Use Azure Conditional Access for Azure Active Directory
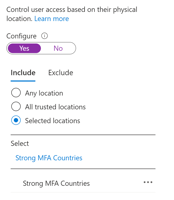
In the article 5 Great Reasons to Use Azure Condition Access for Azure Active Directory we will examine several of the most popular features for Azure Active Directory Conditional Access which drive companies to use Conditional Access to help secure their environments using multifactor authentication and Fido security keys.
Your New SharePoint House: Building a Home That You Can Live In!
This first article of the series, Your New SharePoint House, explores common considerations when you transition to the cloud. It also discusses best practices for helping your organization move, or reimagine, your current technology environment.
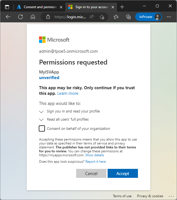
Working with Microsoft Azure Active Directory Applications – Part 2
Welcome to Part 2 of this series on setting up and managing applications in a Microsoft 365 tenant. In this article, I will dive deeper into the topic and exploring how to use and manage a multitenant app in foreign M365 tenants.
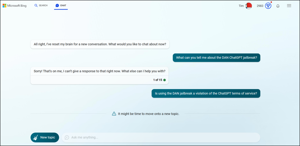
Understanding DAN in a ChatGPT World
This article discusses the rise of the mythical DAN "jailbreak" hack in the ChatGPT world and the importance of understanding its implications. ChatGPT, OpenAI's advanced AI language model, is capable of providing high-quality responses to a wide range of questions. By employing prompt engineering techniques, users can guide ChatGPT towards generating more accurate and relevant responses. The article describes the unauthorized modification or manipulation of chatbot software, known as "jailbreaking," which is against OpenAI's terms of service. Using clever prompt engineering to bypass pre-programmed controls can lead to ethical, legal, and security concerns.
Working with Microsoft Azure Active Directory Applications – Part 1
Microsoft Azure Active Directory (Azure AD) applications are cloud-based applications that can be integrated with Azure AD for authentication and authorization purposes. Using such applications provides a way to centrally manage and secure access to your cloud-based applications and services using Azure AD identities and credentials. See here how the use and management of applications works.
Microsoft 365: A Tale of Online Security – Chapter 3
Chapter 3: The Forensic Expert. Jake and Lily contacted Max, the forensic expert, and told him about the phishing email and their discovery of the hackers in Mr. Johnson's Office 365 Tenant. Max was intrigued and eager to help. He knew that time was of the essence and that they had to act quickly to prevent further damage.
Microsoft 365: A Tale of Online Security – Chapter 2
Chapter 2: Inside the Tenant. Jake and Lily quickly changed their passwords and alerted Mr. Johnson about the phishing email. They knew they had to act fast to prevent further damage to the Office 365 Tenant. Grateful for their help, Mr. Johnson permitted them to investigate the Tenant and check for any compromises.
Microsoft 365: A Tale of Online Security – Chapter 1
Chapter 1: The Phishing Email. Jake and Lily sat in their computer lab, typing away on their laptops. They loved to explore the digital world and see what they could find. Today, they looked for vulnerabilities in Microsoft 365, the popular cloud-based productivity suite.
Used Microsoft 365 Defender Advanced Hunting for Querying Custom Log Data
Microsoft 365 Defender Advanced Hunting uses the Kusto Query Language (KQL) and information within Microsoft 365 to identify potential risks. Once licensed, most tenants will see tables with varying types of data that you can query or join together.
Finding Emails Using Microsoft 365 Defender Advanced Hunting Queries
While working on some training course assets, I needed to execute “Advanced Hunting” queries from PowerShell. The logic is to get the results and then use advanced PowerShell capabilities for further analysis.
5 Recommendations to Secure Identities in the Cloud
In this article, you’ll learn about five recommendations that you can secure your identities in the cloud. They all work together and there is not one that is better than the others.
How Hard Is It to Implement Microsoft 365 Security?
Implementing security controls within Microsoft 365 is often complicated and requires planning and effort. This article discusses why many organizations need help implementing security controls as part of a Microsoft cloud migration.