5 Great Reasons to Use Azure Conditional Access for Azure Active Directory
Microsoft Azure has introduced Azure Active Directory (Azure AD) as their OATH authentication package. Azure Active Directory is used for authentication on all the Microsoft Office 365 and Microsoft Azure features by default. Part of Azure Active Directory’s features is the ability to support multifactor authentication (MFA).
Azure AD supports two different MFA settings. The first is per-user MFA, which allows you to enable MFA for a specific user or all websites and applications. While this is a decent solution, it doesn’t provide for different settings in different circumstances. In order to support these requirements, and others, Microsoft introduced Conditional Access. With Conditional Access the administrator can control the multifactor settings for all users, both the current users as well as future users, without having to enable MFA for each specific user.
The strongest MFA solution that is available through Azure AD involves using the Microsoft Authenticator application on the user’s phone to approve all multifactor requests.
Configure multifactor Authentication (MFA) by Country
One of the popular features within Conditional Access is the ability to set different MFA settings based on the country. By doing this you can configure stronger MFA requirements for countries that are outside of your company’s normal travel. This way, if someone is able to compromise one of the user’s credentials, and that person is in another country (which they probably are) then strict MFA requirements can be enforced for any action that is taken.
In order to configure MFA by country, the first step is to create a known location for the countries which you want the policy to apply to. These named locations can be based on the IP address of the user’s computer, which is attempting to login, or based on the GPS location of the phone that is being used for the Microsoft Authentication application.
Once the named location is created, a Conditional Access policy can be configured. In this policy the location which the policy applies to is then set for this named location as shown in Figure 1.
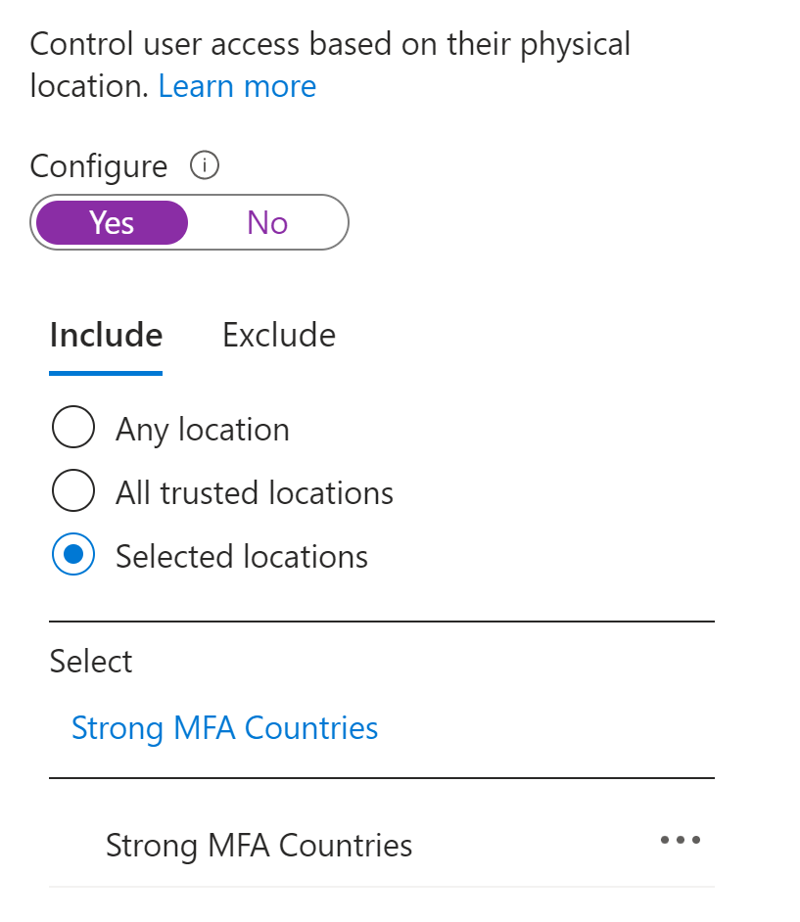
Within the access controls setting of the Conditional Access policy, you can flat out deny access to users from those countries, or you can require basic MFA such as using SMS, or you can limit the options available to the user so that only MFA via the Microsoft Authenticator application, or even via a Fido security key which the user must insert into their computer when prompted.
Blocking Access from Computers Not Owned by the Company
A great option that Conditional Access provides companies that provide computers to their employees (which is basically all the companies out there) is the ability to block logins from devices which aren’t managed by the company. When someone compromises a user’s credentials, they won’t be using a company computer to login. By using the Conditional Access settings that only allow logins on company-owned devices (this requires having Microsoft Intune setup and working correctly on these devices, which is another article on its own right) we can block any login attempts that the attacker is making, simply due to the fact that they are using a computer which isn’t managed by the company.
There are two different levels of “company managed” devices. First there are devices that are configured with Microsoft Intune and managed by Microsoft Intune. Then there are devices that are considered to be “compliant” with Microsoft Intune. These are devices which have a policy within Microsoft Intune where the device meets the requirements of the policy, and the machine matches all of the settings within the policy.
Companies can configure Conditional Access policies for devices which are simply managed by Microsoft Intune, or the company can configure the policy to only allow for devices which are compliant with their Microsoft Intune policies.
High Risk Logins = Strong MFA Requirements
Some newer settings within Conditional Access allow you to use the sign-in risk of the login to determine if the Conditional Access policy will be applied. Risky sign-ins are defined as a new login from a location which would be impossible for the user to travel to since their last login.
A perfect example of this is something which I did recently. I was connected to the console of two different virtual machines for a client; one virtual machine in the West US region, and a second virtual machine in the East US region. On the west coast virtual machine, I opened a browser and logged in to the Azure portal to make some changes. I then closed the browser and started to use the machine in East US, and I needed to make another change to the Azure account. So I opened a web browser on the East US machine and logged in. Since I logged in with the same account, on two different ends of the United States within just a few minutes of each other, my second login was considered suspicious and the Conditional Access policy which was configured for high-risk sign ins was triggered.
Beyond sign-in risk, Microsoft also has user risk as a separate metric. While a sign in can trigger a high risk for itself, this will then increase the risk profile of the specific user. For stronger protection, a policy can be configured for high-risk logins. This means that while the attacker will be stopped, the user of the account will be prompted for additional MFA prompts to ensure that the user of the account is the one who is using the account.
Bypassing MFA in the Office
Many companies want to ensure that multifactor authentication is not used within the office. This is done by creating a named location, similar to the one used in the country settings above. Instead of creating a location for an entire country, the named location is set up based on the IPv4 or IPv6 IP address which the user’s connection is from. Companies will create a named location for each office, with the named location having the public IP addresses of that specific office.
When setting up the conditional access policies you can configure the policy to exclude specific locations as shown in Figure 2.
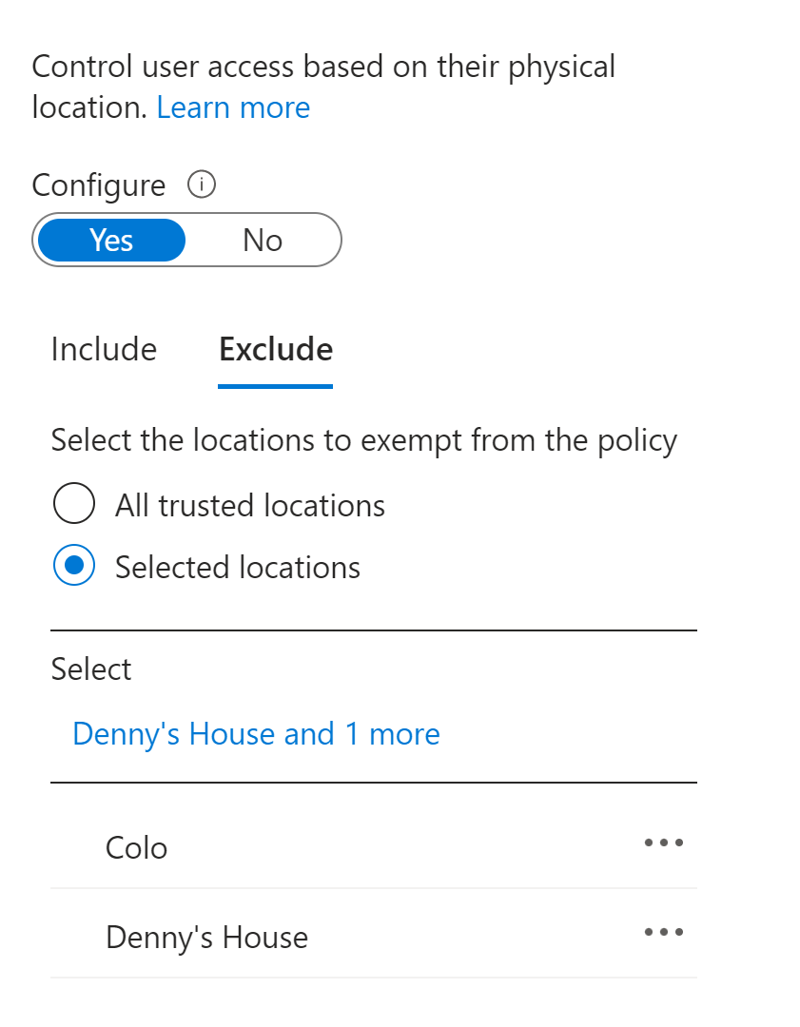
In the sample conditional access policy in Figure 2, the policy forces MFA settings on all locations except for the two locations shown. The other setting shown allows you to exclude all trusted locations (this is a setting you can enable when creating the named location).
Turning MFA On for All Users, Automatically
When using Conditional Access, MFA can be required for a set of users, or all users (my personal preferences) automatically. It doesn’t matter if the user’s account was created before the policy or after the policy. The policies created in Conditional Access apply to all users for whom the policy is configured to target.
Policies can be configured to impact all users, or specific users, either by specific user or by using Azure AD groups. This includes assigned groups, where specific users are assigned to a group, or dynamic groups where users are automatically added and removed from the groups based on a variety of properties on the users’ accounts including parameters as common as the company name, or as unique as the extended attributes that can be configured on those accounts.
Review Conditional Access
If you haven’t reviewed the options that are available in Azure AD Conditional Access, I highly recommend that you do so. If you reviewed Conditional Access options in the past, it will be worth your while to review them again, as Microsoft is regularly improving Conditional Access and adding new features.
One of the newest features for Conditional Access is the ability to use IPv6 addresses as part of the named locations configuration. Just a few short months ago, named locations only supported IPv4 IP addresses, while they now support both IPv4 and IPv6 IP addresses. Microsoft has a very frequent release cycle for Microsoft Azure, with the release cycle as frequent as every six weeks. This means that new features to Conditional Access (and other Microsoft Azure components) can be released every six weeks, so frequent reviews of the available features are worth your time.


