Enhancing Microsoft 365 Security with Conditional Access and Multifactor Authentication
Businesses face challenges in maintaining data integrity and protecting sensitive information. Comprehensive security strategies are essential. Microsoft 365 is a cloud-based suite that offers productivity solutions and a framework for securing corporate data against cyber threats.
However, more than traditional security measures are needed to cope with the sophistication of modern cyber-attacks. That's where advanced security features like multifactor authentication (MFA) and Conditional Access within Microsoft 365 come in. These features are not just add-ons, but essential components of a robust security posture designed to safeguard access to data and applications.
Multifactor authentication enhances security by requiring users to provide two or more verification factors to gain access to resources, thus adding an extra layer of defense against unauthorized access. On the other hand, Conditional Access policies allow organizations to define precise conditions under which users can or cannot access Microsoft 365 services. Together, these tools create a dynamic and responsive security environment that adapts to the complexity of modern cybersecurity challenges.
Multifactor Authentication (MFA)
Multifactor authentication (MFA) is a pivotal defense mechanism that significantly enhances the security of digital assets and sensitive information. It is predicated on the principle that granting access to a system or data should require verification from two or more independent credentials. This verification process uses categories of evidence that are unique to the individual requesting access, categorically segmented into something you know (knowledge), something you have (possession), and something you are (inherence).
Multifactor Authentication Within Microsoft 365
Within the ecosystem of Microsoft 365 (M365), multifactor authentication introduces an additional layer of security, ensuring that accessing emails, documents, and corporate resources extends beyond the mere input of a password. Here's how multifactor authentication functions in Microsoft 365:
- Something you know: This could be a password or a PIN. It's the first factor and the most common form of authentication. However, passwords alone are vulnerable due to the many ways they can be compromised.
- Something you have: This often involves a physical device, such as a smartphone or a security token, that can generate or receive a verification code. Microsoft Authenticator app, for instance, can provide a constantly changing code that's entered as part of the login process.
- Something you are: This involves biometrics, such as fingerprint scans, facial recognition, or retina scans, which add a highly secure layer of authentication that is extremely difficult to replicate or steal.
Multifactor authentication within Microsoft 365 is flexible and user-friendly. It offers various methods to meet users' diverse needs and circumstances while maintaining the system's security integrity.
Benefits of Multifactor Authentication
Implementing MFA within Microsoft 365 provides a multitude of benefits that significantly uplift an organization's security posture:
- Reduced risk of unauthorized access: By requiring multiple forms of verification, MFA makes it exponentially more difficult for unauthorized users to gain access to sensitive systems and data, even if one factor (like a password) is compromised.
- Enhanced protection against phishing: MFA adds layers of security that phishing attempts often cannot bypass.
- Compliance and trust: Many industries require MFA as part of regulatory compliance. Implementing it aligns with these regulations and boosts customer and partner confidence in your security measures.
- Minimal user impact: The Microsoft Authenticator app streamlines the authentication process while adding significant security benefits by designing MFA to be unobtrusive in Microsoft 365.
Implementing Multifactor Authentication in Microsoft 365
Implementing MFA in Microsoft 365 is straightforward and involves configuring security settings within the Entra ID. Organizations can enforce MFA for all users or apply it selectively based on roles, locations, or access requirements. The flexibility of MFA implementation allows organizations to balance security needs with user convenience, ensuring that enhanced security does not impede productivity.
Conditional Access
Conditional access is a pivotal security feature within the Microsoft 365 ecosystem. It acts as a gatekeeper that dynamically evaluates and enforces access controls to applications and data. This policy-driven approach allows administrators to define precise conditions under which users can or cannot access specific resources. Powered by Entra ID, it integrates seamlessly with Microsoft 365, offering a robust framework for implementing a zero-trust security model.
How Conditional Access Works in Microsoft 365
Microsoft 365's Conditional Access uses signals to enforce policies. These signals include user identity, location, device health, service or application, and real-time risk analysis. Based on these signals, Conditional Access policies evaluate requests to access Microsoft 365 resources and apply the appropriate access controls.
The core idea is to provide secure access to resources based on the context of the access attempt. For example, a user attempting to access corporate email from a recognized device within the office may face different restrictions than when accessing an unknown device in a high-risk location.
Benefits of Conditional Access
Implementing Conditional Access within Microsoft 365 offers several benefits:
- Enhanced security posture: By making access decisions based on multiple factors, organizations can significantly reduce the likelihood of unauthorized access, thereby protecting sensitive data and resources.
- Adaptive access policies: Conditional Access allows for creating flexible and adaptive policies, adjusting security requirements based on the context of each access attempt. It ensures a balance between security and user convenience.
- Support for zero-trust security model: Conditional Access is a cornerstone of the zero-trust model, which operates on the principle of "never trust, always verify." Every access request is fully authenticated, authorized, and encrypted before being granted, regardless of where the request originates.
- Automated enforcement of policies: Once set up, Conditional Access policies automatically enforce the predefined rules, reducing the need for manual intervention and allowing IT teams to focus on other critical tasks.
Implementing Conditional Access in Microsoft 365
To implement Conditional Access in Microsoft 365, administrators need to define policies in Entra ID. A typical process involves:
- Identifying the application: Specify the applications or services to which the policy will apply.
- Defining the conditions: Set conditions based on user roles, location, device state, network, or risk levels.
- Setting access controls: Decide on the required controls, such as requiring MFA, blocking access, or requiring device compliance.
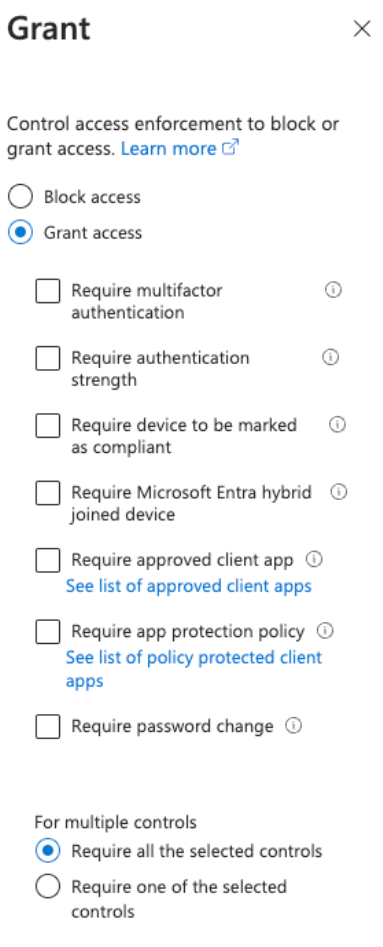
4. Enforcing Policies: Activate the policies to implement them across the specified applications and services.
Administrators can create granular policies that apply to specific scenarios, such as requiring multifactor authentication for users accessing sensitive data outside the corporate network or blocking access from devices that do not comply with corporate security policies.
Examples of Conditional Access Policies
Some practical examples of Conditional Access policies that organizations might implement include:
- Require MFA for external access: Enforce MFA when employees access Microsoft 365 resources outside the corporate network.
- Block access from untrusted locations: Prevent access attempts from high-risk locations or outside predefined geographies.
- Access only from managed devices: Allow access to specific applications only from devices that are managed and compliant with corporate policies.
- Session control for sensitive applications: Implement session restrictions, such as sign-out after a period of inactivity, for applications containing sensitive information.
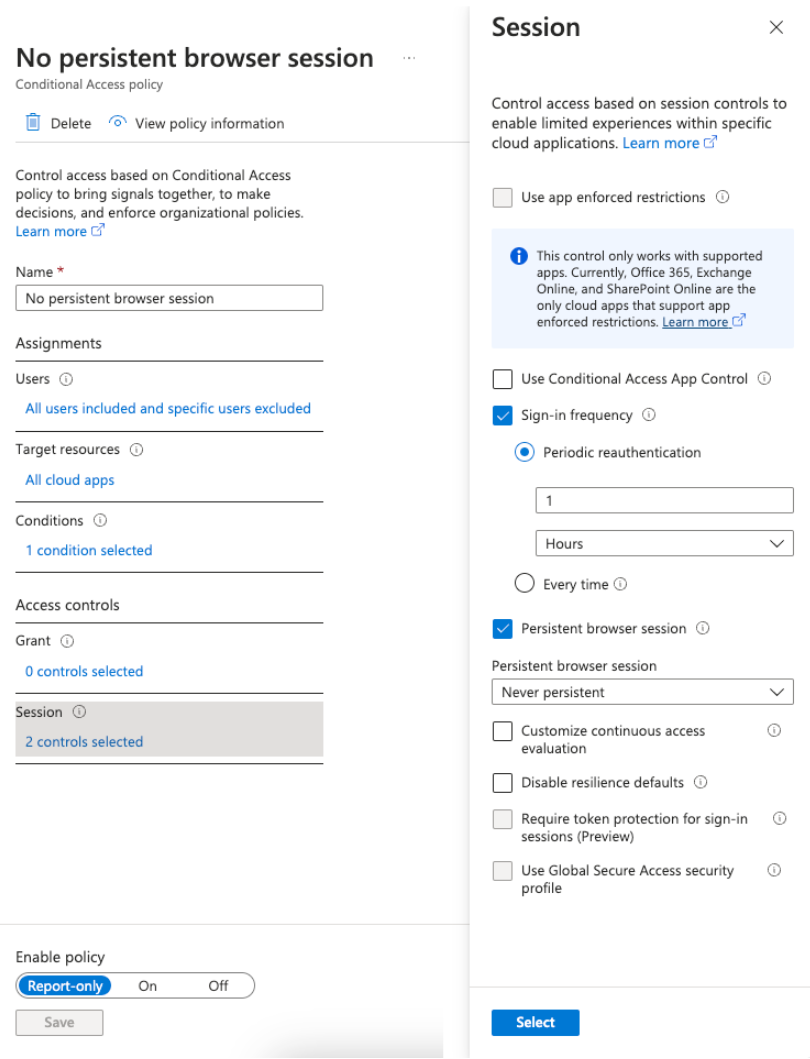
Conditional access is a powerful tool that, when correctly implemented, significantly enhances the security of Microsoft 365 environments.
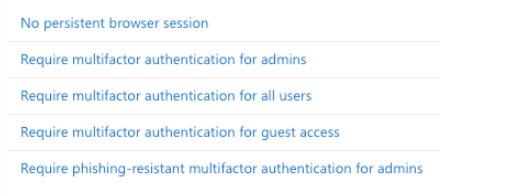
By leveraging the wide range of conditions and controls available, organizations can create a flexible and robust security framework that adapts to their evolving needs.
Authentication Contexts, Sensitivity Labels and Conditional Access
Authentication contexts enable administrators to assign sensitivity levels to specific resources or actions within an application. You can use these sensitivity labels in Conditional Access policies to prompt extra authentication steps or restrict access under certain circumstances. For instance, a document marked with a higher sensitivity level may require stronger authentication methods or be inaccessible from specific locations.
This mechanism operates on the notion that not all data or actions within an application pose the same level of risk. Organizations apply different levels of scrutiny to resources based on their sensitivity, ensuring they use stronger security measures where most needed. This approach avoids needlessly burdening the user or hindering productivity for less sensitive tasks.
Benefits of Using Authentication Contexts with Conditional Access Policies
The use of authentication contexts in Conditional Access policies offers several key advantages:
- Enhanced security for sensitive resources: Organizations can better protect their most critical assets by requiring additional authentication or imposing stricter access controls for high-sensitivity resources.
- Flexible access control: Authentication Contexts enable dynamic access control to adapt based on the access attempt's context, such as the resource's sensitivity, the user's location, or the security posture of the device in use.
- Improved user experience: Users benefit from a seamless access experience for less sensitive resources, with additional authentication prompts only, when necessary, thus balancing security and convenience.
Implementing Authentication Contexts in Microsoft 365
To leverage authentication contexts in Microsoft 365, administrators must first define the contexts within Entra ID. They can then apply these contexts to resources or actions within applications. After defining them, administrators can create Conditional Access policies referencing these contexts to enforce specific access controls.
For example, administrators could create a policy requiring users to access resources tagged with a high-sensitivity context from a compliant device or mandating MFA to verify the user's identity.
Practical Business Scenarios for Using Application Contexts
Practical applications of authentication contexts might include:
- Enhancing protection for financial documents: A policy that requires MFA and device compliance for accessing financial reports or sensitive HR documents.
- Securing access to research data: Implementing stricter access controls, including location-based restrictions, for accessing proprietary research data.
- Differential access based on sensitivity: This policy allows general access to company-wide documents from any location or device but restricts access to sensitive project documents to secure devices in specific locations.
Authentication contexts add a powerful tool to the arsenal of Conditional Access. They allow organizations to fine-tune their access policies based on the data's sensitivity. It ensures that security measures are aligned with the level of risk, enhancing overall protection while maintaining a positive user experience.
To learn more about authentication context, you can read the Microsoft documentation: https://learn.microsoft.com/en-us/entra/identity/conditional-access/concept-conditional-access-cloud-apps#authentication-context
Conclusion
Cyberthreats are on the rise and can be sophisticated. Therefore, it has become increasingly crucial to keep our digital assets secure. Microsoft 365 is a comprehensive suite of productivity tools that provides robust mechanisms to enhance security. Multifactor authentication (MFA) and Conditional Access are the two significant components of modern security strategies that help protect against unauthorized access and ensure that sensitive data remains secure.
Multifactor authentication is an essential security layer that requires users to provide multiple verification forms before granting access. This mechanism significantly reduces the risk of data breaches. On the other hand, Conditional Access further enhances this security model by scrutinizing access requests against predefined policies. This mechanism ensures that only authorized individuals can access your organization's data within the right conditions. Multifactor authentication and Conditional Access form a dynamic and adaptive security posture that can mitigate potential cyber threats.
Call to Action
Implementing multifactor authentication and Conditional Access within Microsoft 365 is a testament to your organization's commitment to security. However, technology alone cannot safeguard against all threats. A holistic approach to security that encompasses policy, education, and technology, is essential. We encourage organizations to:
- Assess your current security posture: Understand where you stand in terms of security and identify potential vulnerabilities.
- Implement MFA and Conditional Access: If not already in place, take steps to implement these critical security features. Start with high-impact, low-effort policies and gradually expand to cover more scenarios and users.
- Educate your users: Security is not just the responsibility of the IT department. Educate your users about the importance of security practices, including their role in protecting organizational data.
- Regularly review and update your security policies: As your organization evolves and new threats emerge, it's essential to periodically review and update your security measures to ensure they remain effective.
Enhancing your Microsoft 365 security with multifactor authentication and Conditional Access is a proactive step toward safeguarding your digital environment against increasingly sophisticated cyber threats. Acting today can ensure a more secure tomorrow for your organization and its stakeholders.


