5 Recommendations to Secure Identities in the Cloud
In this article, you’ll learn about five ways that you can secure your identities in the cloud. I’ll start by discussing what identity and access management (IAM) are to set a foundation. We’ll then go through the five recommendations, which are:
- Zero trust
- Least privilege
- Device management
- Conditional access and risk identification
- User experience
What is cloud identity and access management, and why is it important?
It is important to understand some of the differences around IAM when we're talking about the cloud. The key thing to understand when working with cloud technologies is that we are no longer in charge; our physical four walls are no longer a part of our protection. That is all the responsibility of the cloud provider, so if you're thinking about a defense-in-depth security structure, identity and access becomes your first line of defense. Since that is the area of first importance, the challenge is the protection of identity and access.
We also need to consider the differences between modern versus legacy authentication. The latter focused on being able to protect your network and servers within four walls. With legacy applications, we developed applications for on-premises networks that controlled access to that application. We built an identity database populated with users, which determined the access and permissions each user had to the legacy application.
With modern IAM, an identity provider will manage the access to those applications on-premises and in the cloud. The identity provider maintains a single database of identities to communicate with partners, customers and our employees. All our devices have an identity that is provided by that identity provider. Examples of this are Azure Active Directory, Google IAM and AWS IAM. You can also use other identity providers, such as your LinkedIn profile, to access an application. If you are using LinkedIn as an identity provider, you are using a single set of your email address, password, and security settings to access multiple applications, not just LinkedIn.
We need to manage where those identities are, how we're accessing those resources, and from where you are accessing the various areas and devices.
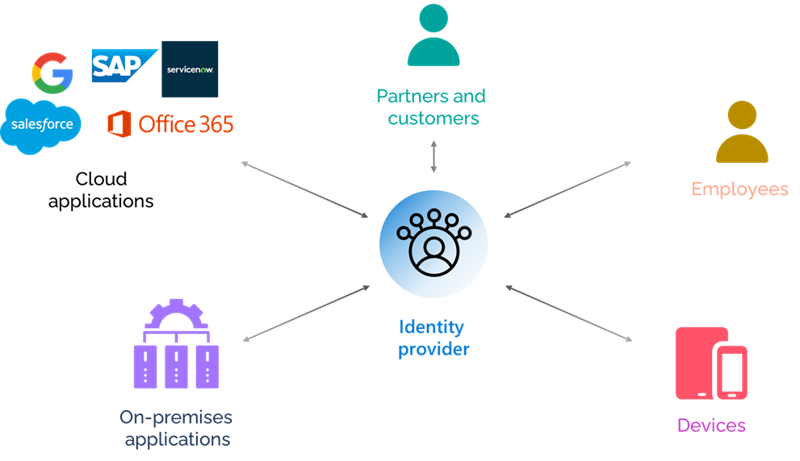
Cloud applications like Office 365, Google Workspace or Salesforce determine how we are utilizing and accessing applications in the cloud and on-premises. We need to understand that the new role of our identities is providing access everywhere and this creates a challenge to how we protect them. That is what the recommendations in this article will cover.
Identity governance is important to consider within your organization. When a user enters the company, they are given access for a particular job role. They may be with that company for 15-20 years and may hold multiple roles within that organization. Once they switch from one job role to another, those permissions should change to reflect the different needs of the job roles. That is the essence of identity governance: governing users’ permissions. For example, maybe someone went from IT to sales. They had highly privileged identities in that IT role, but in a sales role, they should have very limited permissions and limited access to administrative roles. When a user leaves the company, like role changes, the IAM administrators need to govern over those identities and immediately disable their permissions and resource access.
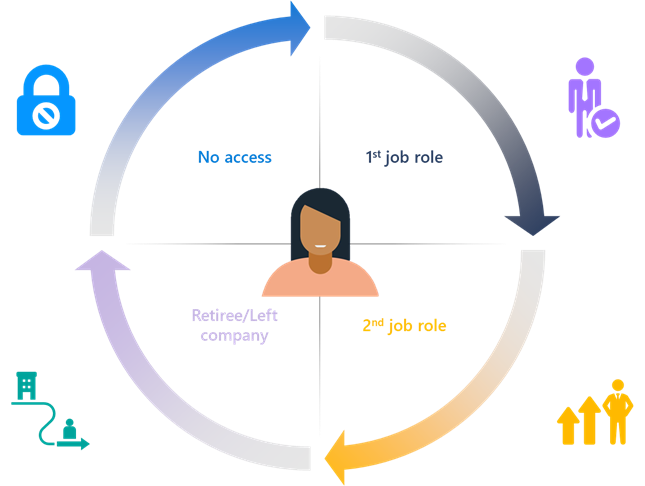
An example where identity governance failed was the 2021 Colonial Pipeline hack in the United States. This organization was attacked when somebody gained access and put ransomware on their servers, holding them hostage for a few days and causing the main oil pipeline for the southeastern part of the United States to essentially shut down. The cause was two people leaving the company who had elevated access rights that were not disabled. They had administrator roles within the organization, and they did not have any type of multi-factor authentication on their accounts. So, the attackers were able to gain the username and password of those individuals and get into the company’s systems. Because the former employees had administrator rights, the attackers were able to go on to actual endpoints and put ransomware on them. An investigation of the hack determined that the identity governance was poor and there was no process for disabling a user that leaves the company.
With that example of poor cloud identity management fresh in our minds, let’s go over five best practices to ensure we avoid such catastrophic failures on our watch.
Recommendation #1: Zero trust
The Colonial Pipeline is a prime example of the need for identity governance, and in particular the zero-trust model. It is important to understand zero trust since many governments are implementing it within their security framework. It is all about verifying continuously and not trusting someone is who they say they are just because they have a correct username and password. This means requiring users to re-verify with multi-factor authentication, password resets or similar measures to access certain applications and resources within an organization.
For example, a person or device may be allowed to browse the web, but if they try to access Salesforce, the HR application or the benefits application, they will be required to verify again who they are to make sure that their identity has not been compromised. Cloud providers have many solutions to make these types of access-based decisions; they also look at IP addresses and where somebody's signing in from.
Recommendation #2: Least privilege
This recommendation is encapsulated in the Figure 2 diagram of identity governance. The end goal here is protecting against potential attacks where someone gains access to your endpoints. Implementing least privilege means using just-in-time access, where outside entities are only given access to devices at the time it is needed. For example, a managed security service provider may need to access a device – generally with Linux devices that's port 22 and with Windows devices that’s port 3389. The secure practice is to set up rules that deny inbound and outbound traffic through those ports by default, and then create a temporary rule that allows access to those devices for the necessary amount of time, then automatically revert to the deny rule after a certain amount of time.
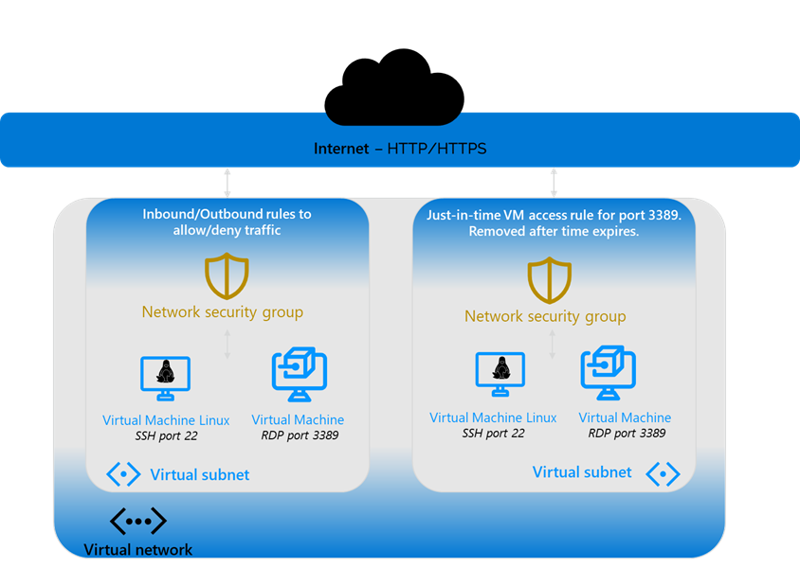
Ideally, you would ask how long they need access; if they say an hour, you set it to expire after an hour. After that time, nobody can access using the device, minimizing the impact of a compromised identity.
Recommendation #3: Device management
Access to resources takes place through devices. These may be company-owned or personal devices. In either case, they should have security controls in place to protect company information. Attackers find ways into networks. Every organization has probably been hacked; if they have not publicly said they have been hacked, they either are lying, or they just don't know yet.
Educating users is extremely important. We will talk more about that in the final recommendation, but users need to understand proper use of devices to protect against attacks. Figure 5 shows how device management tools can protect against users over-exposing company data.
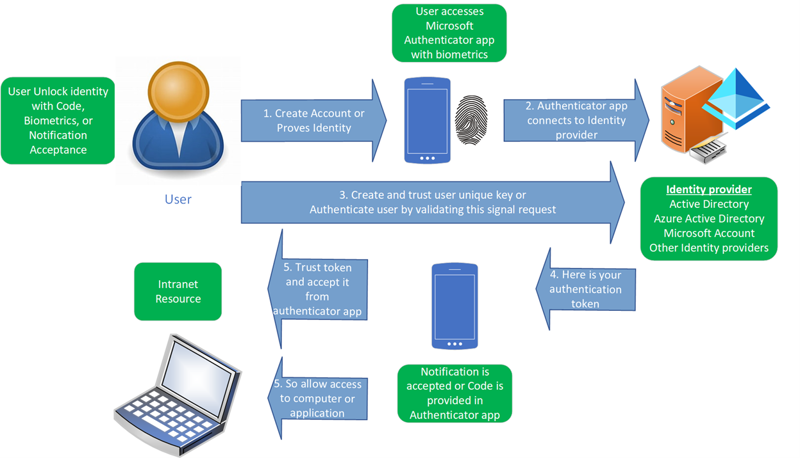
Mobile device management (MDM) and mobile application management (MAM) are ways to protect devices within organizations by using solutions, such as Microsoft Intune, on your device to protect that device. Maybe the users own that device, so they provide MDM for the full level of protection or MAM running on a personal owned device to protect sensitive information from going in the wrong place. Advanced threat protection, OS hardening and encryption using something like BitLocker protects with device encryption. Managed devices can be reviewed for compliance and proper company processes being in place prior to accessing company resources.
Recommendation #4: Conditional access and risk identification
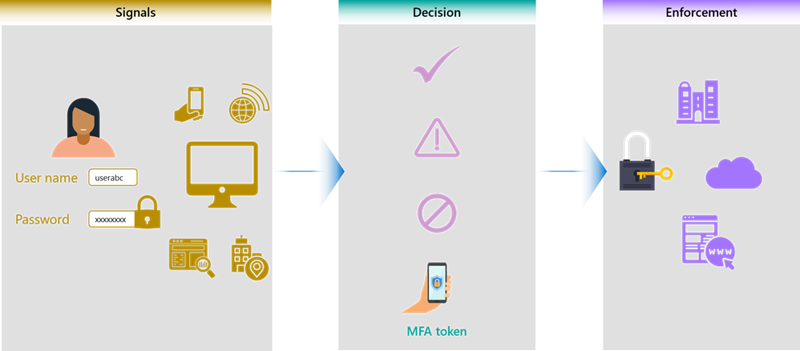
Users and devices have got different conditions; users have got different signals that provide conditional access. Conditional access is a decision-based approach to verifying a person's identity, using greater or lesser measures to do so depending on the conditions under which they're trying to access. Somebody using an unmanaged device that is not using multi-factor authentication on a public Wi-Fi network will need to go through additional verification. If they are accessing an HR application, we are probably going to outright block their access until they are on a trusted network as specified in the cloud providers’ policies. The policies are going to look at the level of risk and provide an alert or additional steps based on the risk identified.
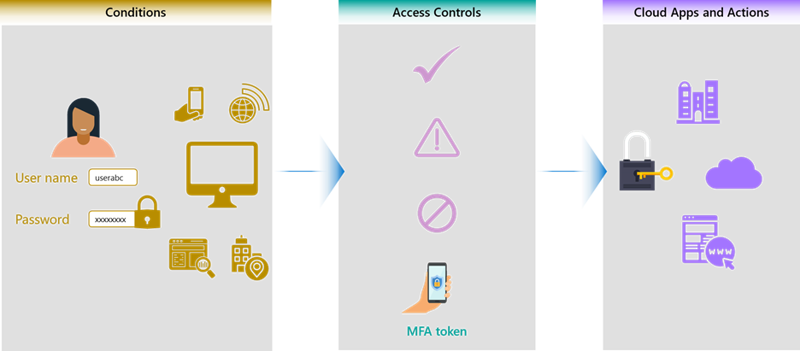
Managing and understanding user risk is a process of recognizing high-risk activity, such as a large number of password attempts, or a user signing in from Michigan in the United States and 15 minutes later, from London, England. Those are all things that should be considered in decision-based access and authorization management for applications.
Recommendation #5: U
ser experiences = user adoption
This last recommendation is all about making sure that users adopt the previous four recommendations. User adoption will be higher if they understand why certain policies for protection are in place and it isn’t difficult for them to gain access to the resources they need. It will also decrease the amount of potential shadow IT, where people within the organization try to “game the system,” or circumvent security processes and policies and put the whole organization at risk. You should proactively educate your user environment about any new security solution that you are putting in place so that they understand what is taking place, why it's taking place, and why it may seem like a hassle in the short term but is worth it in the long run.
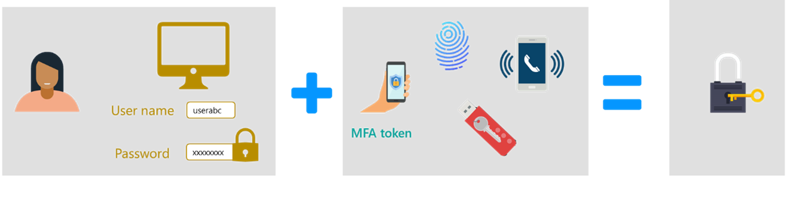
Multi-factor authentication is an example of user education being paramount. As recently as five years ago (2018), when organizations began broadly adopting multi-factor authentication, everyone thought that it was too cumbersome because of the extra step, and they would try to find ways to circumvent multi-factor authentication, putting the entire organization at risk. User acceptance can be increased through education and a simplified solution for verification with MFA.
If we can build an authentication solution that allows users to decrease the number of steps to get access and allows them access to all of their applications with one set of credentials, user adoption will increase. They will not look for shadow IT if it is a seamless experience. User training should be given high priority when implementing a new IAM solution.
Summary
In summary, we have learned about cloud IAM and we provided five recommendations:
- Zero trust
- Least privilege
- Device management
- Conditional access and risk identification
- User experience
They all work together and there is not one that is better than the others. Each of them should be considered, identified and utilized as we build and operate an IAM environment. These are all building blocks that you can put in place to protect users and identities.


