Data and Security Breach Within Microsoft 365
In today's business world, Microsoft 365 has become an indispensable tool for communication, information sharing, and conducting daily operations. This comprehensive suite of productivity tools, cloud services, and software applications provides flexibility and convenience, serving as a virtual office accessible from anywhere and at any time. With applications like Word, Excel, PowerPoint, and Teams, and cloud storage services like OneDrive, Microsoft 365 has become an essential utility for millions of users worldwide.
Data is the lifeblood of organizations and an asset of considerable value. However, with this digital transformation comes an increased need for data security. Security breaches and data leaks can result in substantial financial losses, reputational damage, and regulatory penalties, highlighting the imperative nature of adequate data protection strategies.
As Microsoft 365 is widely used globally and manages a significant amount of data, it, unfortunately, attracts cybercriminals and threat actors who aim to exploit vulnerabilities to gain access to user data. Therefore, it is crucial for organizations that want to utilize this digital suite securely to understand the data and security breaches that occur within Microsoft 365.
Understanding Data and Security Breach
A data breach is when unauthorized individuals access confidential data, often maliciously. It could include sensitive information such as financial details, personal customer data, trade secrets, or intellectual property.
On the other hand, a security breach is a broader concept that refers to any incident where an intruder bypasses the security measures of a system. While this may result in a data breach, it could also involve other disruptive actions, such as implanting malware or causing system failures.
Businesses can face significant consequences from data and security breaches. The financial losses resulting from theft or fraud are just the beginning, as a company's reputation can also suffer. Customers and partners may lose faith in the organization's ability to safeguard their data, which could lead to a loss of business. Additionally, regulatory bodies may impose penalties if the organization fails to comply with data protection standards.
Common Vulnerabilities in Microsoft 365
Although Microsoft 365 has a strong security infrastructure, there are still vulnerabilities that could potentially result in data or security breaches. These vulnerabilities can be quite complex and range from technical issues within the software to inadequate password management by users to the misuse of administrative privileges.
Some common technical vulnerabilities include misconfigured security settings and outdated software. For example, an organization may unintentionally leave specific files or directories open to the public due to incorrect settings in SharePoint or OneDrive. Outdated software versions may also harbor known security flaws, even though newer updates have addressed these flaws, leaving these versions vulnerable to threats.
User behavior significantly contributes to the creation of vulnerabilities. For example, poor password management strategies, including using weak passwords or reusing passwords across multiple platforms, can make it easier for attackers to gain unauthorized access. Similarly, phishing scams can trick users into revealing their login credentials, and threat actors can then use these credentials to infiltrate the system.
Additionally, cyber attackers greatly value administrative accounts that have extensive access privileges. If attackers infiltrate these accounts, it could result in serious outcomes such as data breaches and the potential for additional system exploitation.
Impact of Data and Security Breaches within Microsoft 365
The impact of data and security breaches within Microsoft 365 can be substantial and multifaceted. In 2020, for example, an APT group, "Nobelium," launched a massive phishing campaign that exploited a vulnerability in Microsoft's Power Apps to trick victims into revealing their credentials.
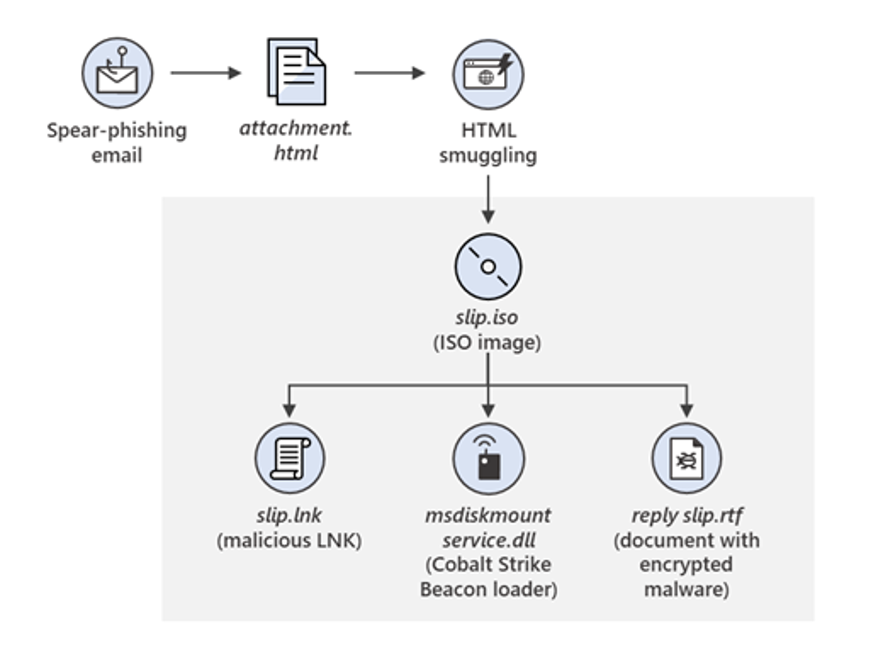
In another incident in 2021, a misconfiguration in the Microsoft Power Platform led to the accidental exposure of millions of records. In another case, an email phishing attack targeted at Microsoft 365 users led to a data breach at a well-known non-profit organization, which leaked sensitive donor information.
Breaches such as these can cause significant financial and reputational damage. The direct financial losses from theft or fraud can be compounded by the cost of investigating the breach, implementing additional security measures, and potentially paying fines for regulatory non-compliance. Moreover, a company's reputation may suffer irreparable harm, as trust is crucial to customer relationships. Customers who lose confidence in an organization's ability to protect their data may take their business elsewhere.
In addition to these consequences, data breaches can also have regulatory implications. With data protection laws such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the U.S., organizations can face hefty fines if they fail to protect customer data adequately or do not comply with reporting obligations following a breach. These laws reinforce the importance of robust data security strategies for the organization's integrity and to avoid potential legal repercussions.
How Do You Identify and Respond to a Microsoft 365 Data and Security Breach?
Identifying Microsoft 365 data or security breach begins with vigilant monitoring of user activities and system alerts. Signs of a potential breach can often be unusual user activities. These might include:
- Repeated failed login attempts.
- Attempts made at odd hours or from unfamiliar locations.
- Unexpected changes in user roles or permissions.
AuditLogs
| where TimeGenerated > ago(30d)
| where OperationName == "Change user password"
| extend InitiatedByJson = parse_json(InitiatedBy)
| project TimeGenerated, User = tostring(InitiatedByJson.user.userPrincipalName), OperationName, Category
| order by TimeGenerated descSimilarly, you should take system alerts seriously, which might relate to installing unfamiliar software or unauthorized changes to system configurations.
One way to detect security breaches is by regularly auditing security logs and reports in Microsoft 365. By using the standard Microsoft 365 Audit logging and Azure AD logs, organizations can investigate user activities, sign-ins, administrative operations, and other useful information. These logs are a great starting point to understand an organization's security status and identify potential problems. However, the amount of data can be overwhelming. Fortunately, the Kusto Query Language (KQL) is a helpful tool to manage the large volume of logs.
Security administrators should consider using KQL querying within Microsoft Purview Advanced Hunting and Microsoft Sentinel for several reasons:
- KQL allows them to formulate sophisticated and precise queries to extract exact information from vast datasets. This precision can help identify potential security threats and anomalies that could go unnoticed with less specific methods.
AADSignInEventsBeta
| where Timestamp > ago(30d)
| where ErrorCode != 0
| where AccountUpn == "nestorw@msdx878906.onmicrosoft.com"
| summarize UnusualSignInCount = count() by ErrorCode, AccountUpn, Country- It facilitates advanced hunting across the organization's data, enabling administrators to proactively seek out security risks rather than simply reacting to them.
- In Microsoft Sentinel, KQL can create custom alerts, improving threat detection efficiency.
- Using KQL in both Microsoft Purview and Microsoft Sentinel provides a consistent language and experience across different Microsoft security tools, enhancing the overall security management process.
For effective auditing, you can adopt the following practices:
- Set a Schedule for Audits: Depending on your organization's needs, you may choose to review your security logs and reports weekly, biweekly, or monthly.
- Understand Your Security Dashboard: It is essential to familiarize yourself with the Microsoft 365 security dashboard and the different alerts and reports.
Microsoft 365 offers a security dashboard that provides insights into security issues. Regularly reviewing this information can help you spot unusual patterns that may indicate a breach. To help with this, consider the following points:
- Monitor User Activities: Pay attention to the User Activities section of the security dashboard. Look for unusual patterns, such as logins from unfamiliar locations or odd hours.
let typicalLocations = dynamic(["US","CA","GB"]);
let timeframe = ago(90d);
AADSignInEventsBeta
| where Timestamp > timeframe
| where ErrorCode == 0
| extend Location = tostring(Country)
| where Location != "" and not(Location in (typicalLocations))
| summarize UnusualSignInCount = count() by Location, AccountDisplayName, Timestamp
| order by Location desc- Check System Alerts: Make it a habit to review the system alerts. Look for unexpected changes in system configurations or installation of unfamiliar software.
- Review User Role Changes: Keep a close eye on changes in user roles or permissions. Unauthorized elevation of user privileges could indicate a breach.
But spotting unusual patterns is just the first step:
- Act on Alerts: Don't ignore alerts. Always investigate them promptly to understand their cause and take corrective action as necessary.
- Seek Expertise When Required: If something seems off and you cannot identify the issue, don't hesitate to seek help from a cybersecurity expert. It is better to be safe than sorry.
Lastly, it is vital to document and learn from your auditing:
- Document and Learn: Record the insights and issues you encounter during these audits. Over time, this can help you understand your system better and spot breaches more efficiently.
Identifying a potential breach requires swift and decisive action to limit its impact. First, temporarily deactivate the affected user accounts or reset their passwords to prevent further unauthorized access. Then, conduct a thorough investigation to understand the scope and nature of the breach. It may involve reviewing activity logs, checking for file or setting changes, and potentially engaging external cybersecurity experts.
When a breach occurs, it is essential to address any security gaps that the attackers may have taken advantage of. This can include implementing stricter security settings, updating software, or educating users on identifying phishing scams. If the breach was due to compromised administrative privileges, it is important to review and refine privilege management policies to ensure that users only have the necessary access.
Finally, communication plays a vital role in managing a breach. Inform affected users and stakeholders about the situation and report the breach to relevant regulatory bodies if necessary. Transparency and open communication can help maintain trust and demonstrate your commitment to security.
The key to managing a Microsoft 365 data and security breach is a blend of preparation, swift action, and continuous learning. Organizations can better protect their data and users by being prepared to identify and respond to breaches.
Mitigating Risks and Enhancing Security
Mitigating risks and enhancing security within Microsoft 365 requires a multi-layered approach. Microsoft 365 implements robust security protocols to safeguard user data and prevent breaches. Here are some key points and actionable measures to consider:
- Implement robust password policies: Encourage users to create complex passwords and enable multi-factor authentication for added security.
- Regularly update software and applications: Install the latest updates and security patches to address vulnerabilities.
- Utilize data loss prevention (DLP) policies: Define and enforce policies that prevent sensitive data from being accidentally or maliciously leaked.
- Enable email filtering and anti-phishing measures: Utilize tools to detect and block phishing attempts and suspicious email content.
- Implement privileged access management (PAM): Limit administrative access to only those who require it and regularly review and audit privileges.
- Provide comprehensive security training: Educate users about the risks of phishing attacks, social engineering, and the importance of secure practices.
- Promote password best practices: Encourage users to use unique, strong passwords and discourage password sharing or reuse.
- Raise awareness about email and attachment safety: Teach users to scrutinize email senders, avoid clicking suspicious links, and be cautious when opening attachments.
- Conduct simulated phishing exercises: Test user awareness through phishing campaigns to identify areas for improvement and provide targeted training.
- Encourage reporting suspicious activities: Establish a straightforward process for users to report potential security incidents or breaches.
Organizations can improve their defenses against data breaches in Microsoft 365 by utilizing Microsoft's security protocols, implementing additional security measures, and educating users. It is crucial to take proactive and ongoing measures to mitigate risks and enhance security, especially in the constantly changing field of cybersecurity.
Conclusion
Understanding and mitigating data and security breaches within Microsoft 365 is paramount in today's digital landscape. The widespread use of Microsoft 365 and the value of the data it manages make it an attractive target for threat actors. Taking proactive measures to safeguard sensitive information and ensure the system's integrity is crucial.
Both Microsoft and its IT and Security Administrators share the responsibility for maintaining security. Microsoft is crucial in continuously enhancing its security protocols, promptly addressing vulnerabilities, and providing tools and resources to help organizations protect their data. At the same time, IT and Security Administrators must stay informed about best security practices, adopt additional security measures, and actively participate in ongoing education and training.
Protecting data and preventing breaches is a team effort that requires collaboration. To achieve this, Microsoft provides vital security measures, organizations add extra protective measures, and IT and Security Administrators must remain vigilant. By working together, you can reduce risks and maintain a secure environment within Microsoft 365, allowing users to benefit from its productivity features confidently.


